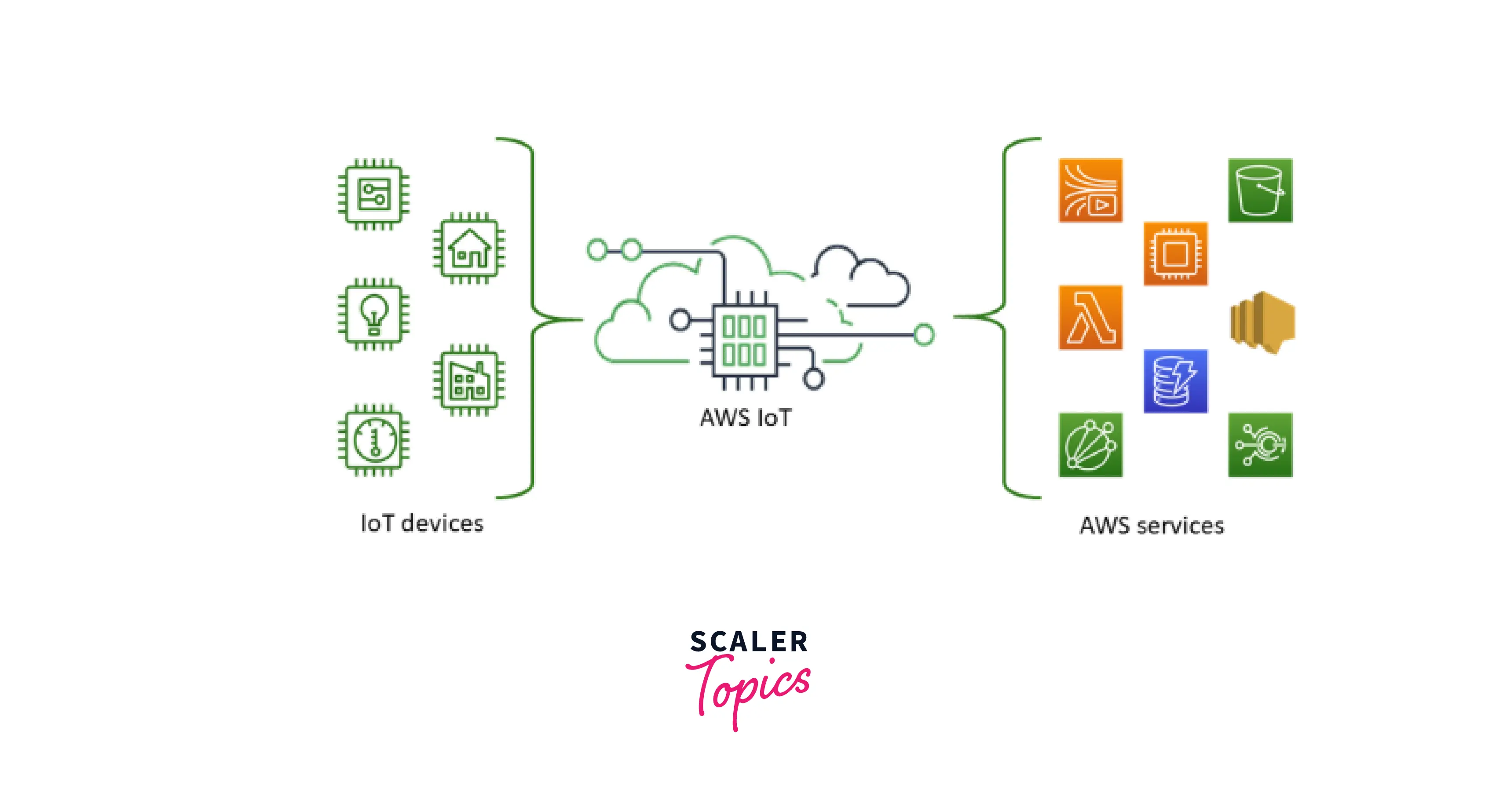
AWS IoT Core SSH provides a robust solution for connecting, monitoring, and managing IoT devices in a secure and scalable manner. As businesses increasingly rely on IoT to drive innovation and operational efficiency, understanding how to leverage AWS IoT Core SSH becomes a key differentiator. With its ability to facilitate secure communication between devices and cloud infrastructure, AWS IoT Core SSH ensures that your IoT ecosystem remains both reliable and protected. The integration of AWS IoT Core SSH into your IoT architecture offers numerous benefits, including enhanced security, simplified device management, and seamless scalability. By enabling secure shell (SSH) access to IoT devices, AWS IoT Core allows administrators to troubleshoot, configure, and manage devices remotely without compromising security. This functionality is particularly valuable for organizations operating in industries such as manufacturing, healthcare, and logistics, where IoT devices are deployed across distributed environments. With AWS IoT Core SSH, businesses can ensure that their IoT infrastructure remains resilient against cyber threats while maintaining operational efficiency. As we delve deeper into this guide, we will explore the various features, use cases, and best practices for AWS IoT Core SSH. Whether you’re an IoT developer, system administrator, or business leader, this article will equip you with the knowledge and tools to harness the full potential of AWS IoT Core SSH. From understanding the underlying technology to implementing advanced configurations, we’ll cover everything you need to know to optimize your IoT management strategy. By the end of this guide, you’ll be well-prepared to integrate AWS IoT Core SSH into your operations and drive meaningful outcomes for your organization.
Table of Contents
- What is AWS IoT Core SSH and Why Should You Care?
- How Does AWS IoT Core SSH Work Under the Hood?
- Key Features of AWS IoT Core SSH
- What Are the Top Use Cases for AWS IoT Core SSH?
- What Benefits Does AWS IoT Core SSH Offer for IoT Management?
- Best Practices for Implementing AWS IoT Core SSH
- What Are the Common Challenges with AWS IoT Core SSH and How to Overcome Them?
- What Does the Future Hold for AWS IoT Core SSH?
What is AWS IoT Core SSH and Why Should You Care?
AWS IoT Core SSH is a powerful feature within Amazon Web Services (AWS) that allows secure shell (SSH) access to IoT devices managed through AWS IoT Core. This functionality enables administrators to establish encrypted connections with IoT devices, facilitating secure remote management and troubleshooting. By leveraging SSH protocols, AWS IoT Core ensures that sensitive data exchanged between devices and the cloud remains protected from unauthorized access.
The importance of AWS IoT Core SSH cannot be overstated, especially in today’s interconnected world. With billions of IoT devices deployed globally, ensuring secure communication is paramount. AWS IoT Core SSH addresses this challenge by providing a secure channel for device management, reducing the risk of cyberattacks and data breaches. This is particularly crucial for industries such as healthcare, where IoT devices often handle sensitive patient information, or manufacturing, where downtime caused by security breaches can result in significant financial losses.
Read also:Christine Baumgartner A Comprehensive Look Into Her Life Career And Legacy
Moreover, AWS IoT Core SSH is not just about security; it also enhances operational efficiency. By enabling remote access to IoT devices, administrators can troubleshoot issues, apply updates, and configure settings without needing physical access to the devices. This capability is invaluable for organizations with geographically dispersed IoT deployments, as it reduces travel costs and minimizes downtime. Additionally, AWS IoT Core SSH integrates seamlessly with other AWS services, allowing businesses to build a comprehensive IoT management strategy that aligns with their broader cloud infrastructure.
How Does AWS IoT Core SSH Work Under the Hood?
At its core, AWS IoT Core SSH relies on a combination of encryption protocols, authentication mechanisms, and secure communication channels to ensure the integrity and confidentiality of data exchanged between IoT devices and the cloud. The process begins with the establishment of a secure connection using SSH, which encrypts all data transmitted between the device and the AWS IoT Core platform. This encryption ensures that even if data is intercepted, it cannot be deciphered by unauthorized parties.
The authentication process is another critical component of AWS IoT Core SSH. Devices must first be registered with AWS IoT Core, where they are assigned unique credentials, such as certificates or keys. These credentials are used to verify the identity of the device during the SSH connection process. AWS IoT Core also supports role-based access control, allowing administrators to define granular permissions for different users or devices. This ensures that only authorized individuals can access specific IoT devices or perform certain actions.
Once the connection is established, administrators can use SSH to execute commands, transfer files, or monitor device performance. AWS IoT Core SSH supports a wide range of SSH clients, making it compatible with various operating systems and devices. Additionally, AWS provides detailed logging and monitoring capabilities, enabling administrators to track SSH sessions and identify potential security threats. By combining robust encryption, authentication, and monitoring, AWS IoT Core SSH ensures that IoT devices remain secure and accessible at all times.
Key Features of AWS IoT Core SSH
AWS IoT Core SSH offers a variety of features that make it a versatile and powerful tool for IoT management. One of its standout features is its ability to integrate seamlessly with AWS IoT Core’s device management capabilities. This integration allows administrators to manage device registries, apply firmware updates, and monitor device health directly through the AWS Management Console.
Another key feature is its support for multi-factor authentication (MFA), which adds an extra layer of security to SSH connections. By requiring users to provide additional verification, such as a one-time password or biometric data, MFA reduces the risk of unauthorized access. AWS IoT Core SSH also supports automated session termination, which ensures that idle connections are closed after a specified period, further enhancing security.
Read also:Debra Jo Rupps Kids A Glimpse Into Her Family Life And More
Additionally, AWS IoT Core SSH provides extensive logging and auditing capabilities. Administrators can track SSH sessions, monitor user activities, and generate detailed reports for compliance purposes. This level of transparency not only helps organizations meet regulatory requirements but also enables them to identify and address potential security vulnerabilities proactively.
What Are the Top Use Cases for AWS IoT Core SSH?
AWS IoT Core SSH is a versatile tool that can be applied across a wide range of industries and use cases. One of the most common applications is in the field of predictive maintenance. By enabling remote access to IoT sensors and devices, AWS IoT Core SSH allows maintenance teams to monitor equipment performance in real-time and identify potential issues before they lead to costly downtime. This proactive approach not only improves operational efficiency but also extends the lifespan of critical assets.
Another prominent use case is in the healthcare industry, where AWS IoT Core SSH is used to manage medical devices such as patient monitors, infusion pumps, and imaging equipment. By providing secure remote access, healthcare providers can ensure that these devices remain operational and compliant with regulatory standards. This capability is particularly valuable in remote or underserved areas, where physical access to medical devices may be limited.
Finally, AWS IoT Core SSH is widely used in smart city initiatives, where IoT devices are deployed to monitor and manage infrastructure such as traffic lights, public transportation systems, and environmental sensors. By enabling secure remote management, AWS IoT Core SSH helps city planners optimize resource allocation, reduce energy consumption, and improve the quality of life for residents.
Industrial Automation
In the realm of industrial automation, AWS IoT Core SSH plays a crucial role in managing programmable logic controllers (PLCs), robotic systems, and other IoT-enabled machinery. By providing secure remote access, manufacturers can streamline production processes, reduce downtime, and enhance overall efficiency.
Smart Agriculture
Smart agriculture is another area where AWS IoT Core SSH is making a significant impact. By enabling remote access to IoT sensors that monitor soil moisture, temperature, and crop health, farmers can optimize irrigation schedules, reduce water consumption, and improve crop yields.
What Benefits Does AWS IoT Core SSH Offer for IoT Management?
The adoption of AWS IoT Core SSH offers numerous benefits for organizations looking to enhance their IoT management capabilities. One of the most significant advantages is improved security. By encrypting all data transmitted between devices and the cloud, AWS IoT Core SSH ensures that sensitive information remains protected from cyber threats. This is particularly important in industries such as finance and healthcare, where data breaches can have severe consequences.
Another key benefit is increased operational efficiency. With AWS IoT Core SSH, administrators can manage IoT devices remotely, reducing the need for on-site visits and minimizing downtime. This capability is particularly valuable for organizations with large-scale IoT deployments, as it allows them to scale their operations without incurring additional costs.
Finally, AWS IoT Core SSH enhances flexibility and scalability. By integrating seamlessly with other AWS services, such as AWS Lambda and Amazon S3, organizations can build a comprehensive IoT management strategy that aligns with their broader cloud infrastructure. This flexibility enables businesses to adapt to changing market conditions and technological advancements, ensuring that their IoT ecosystem remains future-proof.
Best Practices for Implementing AWS IoT Core SSH
To maximize the benefits of AWS IoT Core SSH, it’s essential to follow best practices for implementation. One of the most critical steps is to ensure that all devices are registered with AWS IoT Core and assigned unique credentials. These credentials should be stored securely and rotated regularly to minimize the risk of unauthorized access.
Another best practice is to enable multi-factor authentication (MFA) for all SSH connections. By requiring users to provide additional verification, such as a one-time password or biometric data, MFA adds an extra layer of security. Additionally, administrators should configure automated session termination to ensure that idle connections are closed after a specified period.
Finally, organizations should take advantage of AWS IoT Core’s logging and monitoring capabilities. By tracking SSH sessions and monitoring user activities, administrators can identify potential security threats and address them proactively. Regular audits and compliance checks should also be conducted to ensure that all security policies are being followed.
What Are the Common Challenges with AWS IoT Core SSH and How to Overcome Them?
While AWS IoT Core SSH offers numerous benefits, organizations may encounter challenges during implementation. One common issue is the complexity of managing multiple devices and credentials. To address this, organizations can use AWS IoT Core’s device management capabilities to automate tasks such as device registration, credential rotation, and firmware updates.
Another challenge is ensuring compliance with regulatory standards. Many industries, such as healthcare and finance, have strict requirements for data security and privacy. To overcome this, organizations should leverage AWS IoT Core’s logging and auditing capabilities to track SSH sessions and generate detailed reports for compliance purposes.
Finally, organizations may face challenges related to scalability. As IoT deployments grow, managing SSH connections for thousands or even millions of devices can become overwhelming. To address this, organizations can use AWS IoT Core’s integration with other AWS services, such as AWS Lambda and Amazon S3, to build a scalable and flexible IoT management strategy.
Device Management Complexity
Managing a large number of IoT devices can be challenging, especially when it comes to maintaining accurate device registries and rotating credentials. AWS IoT Core’s automated device management features can help streamline these tasks and reduce the burden on administrators.
Regulatory Compliance
Compliance with regulatory standards is a critical concern for many organizations. AWS IoT Core’s logging and auditing capabilities provide the transparency needed to meet these requirements and ensure that all security policies are being followed.
What Does the Future Hold for AWS IoT Core SSH?
As IoT continues to evolve, so too will the capabilities of AWS IoT Core SSH. One emerging trend is the integration of artificial intelligence (AI) and machine learning (ML) into IoT management. By leveraging AI and ML, organizations can gain deeper insights into device performance, predict potential issues, and automate routine tasks.
Another trend is the growing adoption of edge computing. By processing data closer to the source, edge computing reduces latency and improves performance. AWS IoT Core SSH is well-positioned to support this trend by enabling secure remote access to edge devices and ensuring that data remains protected.
Finally, as IoT deployments become increasingly complex, the demand for scalable and flexible solutions will continue to grow. AWS IoT Core SSH’s integration with other AWS services ensures that organizations can build a comprehensive IoT management strategy that meets their evolving needs.
FAQs
What is AWS IoT Core SSH?
AWS IoT Core SSH is a feature that enables secure shell (SSH) access to IoT devices managed through AWS IoT Core. It allows administrators to establish encrypted connections for remote management and troubleshooting.
How does AWS IoT Core SSH enhance security?
AWS IoT Core SSH enhances security by encrypting all data transmitted between devices and the cloud, requiring unique credentials for authentication, and supporting multi-factor authentication (MFA) for additional protection.
Can AWS IoT Core SSH be used for large-scale IoT deployments?
Yes