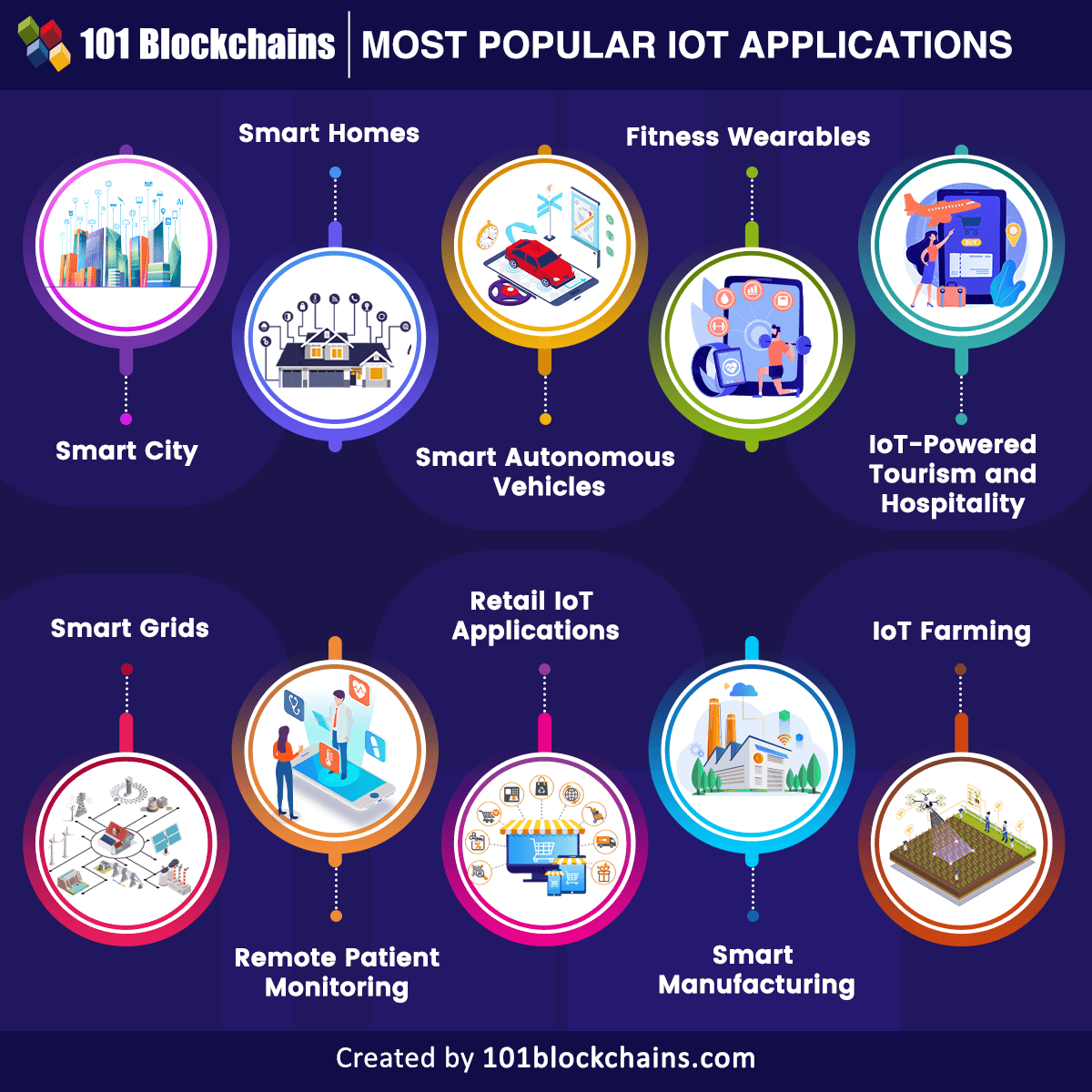
In today's hyper-connected world, the integration of Internet of Things (IoT) and Secure Shell (SSH) has revolutionized the way we interact with technology. From smart homes to industrial automation, IoT SSH applications are becoming increasingly vital for secure and efficient device management. These applications enable secure remote access, configuration, and monitoring of IoT devices, ensuring both convenience and safety in an ever-expanding digital landscape. As businesses and consumers alike embrace the IoT revolution, understanding the role of SSH in this ecosystem becomes crucial for harnessing its full potential.
The significance of IoT SSH applications extends far beyond simple device connectivity. These applications provide a robust framework for secure communication between devices, networks, and users. With the number of connected devices expected to reach 75 billion by 2025, the need for secure management solutions has never been more pressing. SSH protocols offer encrypted channels that protect sensitive data while enabling administrators to maintain control over distributed IoT networks, making them an essential component of modern IoT infrastructure.
As we delve deeper into the realm of IoT SSH applications, it's important to recognize how these technologies are transforming various industries. From healthcare to manufacturing, the combination of IoT and SSH is driving innovation while addressing critical security concerns. This comprehensive guide will explore the multifaceted aspects of IoT SSH applications, providing valuable insights into their implementation, benefits, and future potential in our increasingly connected world.
Read also:Christian Kane Hollywoods Renaissance Man Ndash The Ultimate Guide
Table of Contents
- What Are IoT SSH Applications and Why Do They Matter?
- Key Components and Architecture of IoT SSH Systems
- How Do IoT SSH Applications Work in Practice?
- What Are the Primary Benefits of Using IoT SSH Applications?
- What Security Challenges Do IoT SSH Applications Face?
- Implementation Best Practices for IoT SSH Applications
- Future Trends in IoT SSH Application Development
- Frequently Asked Questions About IoT SSH Applications
What Are IoT SSH Applications and Why Do They Matter?
IoT SSH applications represent the convergence of two powerful technologies that have become fundamental to modern computing. At its core, Secure Shell (SSH) is a cryptographic network protocol designed to provide secure access to network services over unsecured networks. When applied to the Internet of Things ecosystem, SSH becomes a crucial tool for managing the vast array of connected devices that comprise IoT networks. These applications enable administrators to securely access, configure, and monitor IoT devices remotely, ensuring both operational efficiency and data security.
The importance of IoT SSH applications stems from their ability to address several critical challenges in IoT management. First and foremost, they provide a secure communication channel between IoT devices and management systems, protecting sensitive data from unauthorized access and cyber threats. This security feature is particularly crucial given the increasing number of IoT devices in various sectors, from smart cities to industrial automation. Additionally, IoT SSH applications enable centralized management of distributed devices, reducing the complexity of maintaining large-scale IoT deployments.
Several key components make up the foundation of IoT SSH applications. These include authentication mechanisms, encryption protocols, and secure tunneling capabilities. The authentication process typically involves public-key cryptography, where each device has a unique key pair for secure identification. Encryption protocols ensure that all data transmitted between devices and management systems remains confidential and tamper-proof. Secure tunneling capabilities allow administrators to establish encrypted connections through firewalls and other network barriers, enabling seamless remote management of IoT devices regardless of their physical location.
Key Components and Architecture of IoT SSH Systems
Core Elements of IoT SSH Infrastructure
The architecture of IoT SSH applications comprises several fundamental components that work together to create a secure and efficient management ecosystem. At the foundation lies the SSH server, which operates on each IoT device, listening for incoming secure connections. This server component handles authentication requests, manages encryption keys, and facilitates secure data transfer. Alongside the server, the SSH client serves as the interface through which administrators interact with IoT devices, providing command-line access and file transfer capabilities.
Authentication and Authorization Mechanisms
Security in IoT SSH applications heavily relies on robust authentication and authorization systems. These mechanisms typically employ multi-layered approaches, combining password-based authentication with public-key infrastructure (PKI). The PKI system generates unique key pairs for each device, where the private key remains securely stored on the device while the public key is registered with the management system. This dual-key system ensures that only authorized users with the corresponding private key can access the device, significantly reducing the risk of unauthorized access.
Encryption Protocols and Data Protection
Data protection in IoT SSH applications utilizes advanced encryption protocols to safeguard information during transmission. The system employs symmetric encryption for data transfer, using algorithms like AES (Advanced Encryption Standard) to ensure both speed and security. Additionally, asymmetric encryption handles key exchange and authentication processes, providing an extra layer of security through methods such as RSA (Rivest-Shamir-Adleman) or ECC (Elliptic Curve Cryptography). These encryption protocols work in tandem to create a secure communication channel that protects against various cyber threats, including man-in-the-middle attacks and data interception.
Read also:The Inspiring Life Of Adrienne Armstrong An Influential Figure Who Changed The Game
How Do IoT SSH Applications Work in Practice?
The operational mechanics of IoT SSH applications follow a well-defined process that ensures secure and efficient device management. When an administrator initiates a connection to an IoT device, the SSH client first establishes a secure channel by performing a handshake with the SSH server running on the target device. This handshake process involves several crucial steps: protocol negotiation, key exchange, and authentication verification. During protocol negotiation, both client and server agree on the encryption algorithms and protocols to be used for the session, ensuring compatibility and optimal security.
Once the initial handshake is complete, the authentication process begins. The SSH client presents its credentials, typically in the form of a public key or password, which the SSH server verifies against its authorized keys database. Upon successful authentication, the system establishes an encrypted session using symmetric encryption keys derived from the initial key exchange. This encryption ensures that all subsequent communications between the client and server remain confidential and protected from potential eavesdroppers or attackers.
Throughout the session, IoT SSH applications maintain several security mechanisms to protect against various threats. The system continuously monitors the connection for signs of tampering or unauthorized access attempts. Additionally, SSH applications implement mechanisms for secure file transfer (SFTP) and port forwarding, allowing administrators to safely transfer configuration files or access network services through encrypted tunnels. These features prove particularly valuable in industrial IoT applications, where secure remote management of critical infrastructure is paramount.
What Are the Primary Benefits of Using IoT SSH Applications?
IoT SSH applications offer numerous advantages that significantly enhance both operational efficiency and security in IoT ecosystems. One of the most prominent benefits is the ability to manage devices remotely with confidence. Administrators can securely access and configure IoT devices from anywhere in the world, eliminating the need for physical presence during maintenance or troubleshooting operations. This remote management capability translates to substantial cost savings and improved response times, especially for organizations with geographically distributed IoT deployments.
Another crucial advantage lies in the enhanced security features provided by IoT SSH applications. The robust encryption protocols and authentication mechanisms create a secure environment that protects sensitive data and prevents unauthorized access. This security layer becomes increasingly important as IoT devices often handle critical information in sectors such as healthcare, finance, and industrial automation. Furthermore, the secure tunneling capabilities of SSH applications enable administrators to bypass network restrictions and firewalls safely, ensuring uninterrupted access to IoT devices regardless of network topology.
From an operational perspective, IoT SSH applications contribute to improved system reliability and uptime. The ability to quickly address configuration issues or perform software updates remotely helps prevent potential downtime and ensures consistent device performance. Additionally, these applications facilitate automated monitoring and maintenance tasks, allowing administrators to implement proactive maintenance strategies that can detect and resolve issues before they impact system functionality. This combination of security, accessibility, and operational efficiency makes IoT SSH applications an indispensable tool for modern IoT management.
What Security Challenges Do IoT SSH Applications Face?
Despite their robust security features, IoT SSH applications encounter several significant challenges in maintaining secure operations. One of the primary concerns revolves around key management and storage. As the number of IoT devices grows exponentially, managing and securing private keys across thousands or even millions of devices becomes increasingly complex. The risk of key compromise escalates when devices are deployed in physically insecure locations, where attackers might attempt to extract private keys through hardware attacks or other sophisticated methods.
Common Vulnerabilities in IoT SSH Implementations
Several specific vulnerabilities frequently appear in IoT SSH applications, often stemming from implementation oversights or configuration errors. Weak password policies, despite the availability of public-key authentication, remain a persistent issue, particularly in consumer-grade IoT devices. Additionally, many devices ship with default SSH credentials or pre-installed keys that aren't changed during initial setup, creating easy entry points for attackers. The lack of regular security updates and patch management in many IoT devices further compounds these vulnerabilities, leaving systems exposed to known exploits.
Emerging Threats and Mitigation Strategies
The evolving threat landscape presents new challenges for IoT SSH applications, including advanced persistent threats and sophisticated malware specifically targeting SSH protocols. Attackers increasingly employ techniques such as brute-force attacks, credential stuffing, and man-in-the-middle attacks to compromise SSH connections. To combat these threats, organizations must implement comprehensive security strategies that go beyond basic SSH configuration. This includes implementing multi-factor authentication, regularly rotating keys, and employing intrusion detection systems specifically designed to monitor SSH traffic for suspicious activity.
Best Practices for Secure SSH Configuration
Several key practices can significantly enhance the security of IoT SSH applications. First, organizations should disable password authentication entirely, relying solely on public-key authentication. Regularly updating SSH software and cryptographic libraries ensures protection against newly discovered vulnerabilities. Implementing strict access control policies, including IP whitelisting and time-based access restrictions, helps limit potential attack surfaces. Additionally, monitoring and logging all SSH access attempts provides valuable insights into potential security incidents and helps maintain compliance with regulatory requirements.
Implementation Best Practices for IoT SSH Applications
Successful deployment of IoT SSH applications requires careful planning and adherence to established best practices. The implementation process typically begins with a comprehensive security assessment, identifying potential vulnerabilities and establishing appropriate security baselines. Organizations should create a detailed deployment plan that includes device inventory management, key distribution strategies, and access control policies. This planning phase should also address scalability considerations, ensuring the SSH infrastructure can accommodate future growth in IoT deployments.
Step-by-Step Implementation Guide
The implementation process follows a structured approach that maximizes security while maintaining operational efficiency. First, administrators must generate unique key pairs for each IoT device, storing private keys securely and registering public keys with the management system. Next, SSH servers should be configured with strict security parameters, including disabling root login, implementing key-only authentication, and setting appropriate timeout values. The configuration should also include proper firewall rules and network segmentation to isolate IoT devices from other network segments.
During the deployment phase, organizations should establish centralized management systems for monitoring and maintaining SSH configurations across all devices. This includes implementing automated tools for key rotation, configuration auditing, and security patch management. Regular security audits and penetration testing should be scheduled to identify and address potential vulnerabilities. Additionally, staff training programs should be developed to ensure administrators understand proper SSH usage and security protocols.
Optimization Strategies for Large-Scale Deployments
For organizations managing large IoT networks, several optimization strategies can enhance SSH application performance and security. Implementing certificate-based authentication can streamline key management while maintaining high security standards. Using SSH bastion hosts or jump servers can centralize access control and simplify auditing processes. Organizations should also consider implementing SSH tunneling for secure communication between IoT devices and backend systems, reducing the risk of data interception during transmission.
Future Trends in IoT SSH Application Development
What Emerging Technologies Are Shaping the Future of IoT SSH Applications?
The future of IoT SSH applications is being shaped by several groundbreaking technological advancements that promise to enhance both security and functionality. Quantum-resistant cryptography is emerging as a crucial development, addressing concerns about the potential vulnerability of current encryption algorithms to quantum computing attacks. This new generation of cryptographic protocols will ensure that IoT SSH applications remain secure even as quantum computing becomes more prevalent. Additionally, the integration of artificial intelligence and machine learning algorithms is revolutionizing how SSH applications detect and respond to security threats in real-time.
How Will 5G and Edge Computing Impact IoT SSH Applications?
The widespread adoption of 5G networks and edge computing architecture is set to transform IoT SSH applications in significant ways. 5G's ultra-low latency and high bandwidth capabilities enable more responsive and reliable SSH connections, even for resource-constrained IoT devices. Edge computing, meanwhile, allows for localized processing and decision-making, reducing the need for constant cloud connectivity and enabling more efficient SSH-based device management. This combination of technologies will facilitate more sophisticated remote management capabilities while maintaining robust security standards.
Blockchain Integration and Decentralized Security Models
Blockchain technology is emerging as a potential game-changer for IoT SSH applications, offering new possibilities for decentralized authentication and access control. By leveraging blockchain's immutable ledger and smart contract capabilities, organizations can create more transparent and secure systems for managing SSH keys and access permissions. This decentralized approach could eliminate single points of failure and provide enhanced protection against various types of cyber attacks