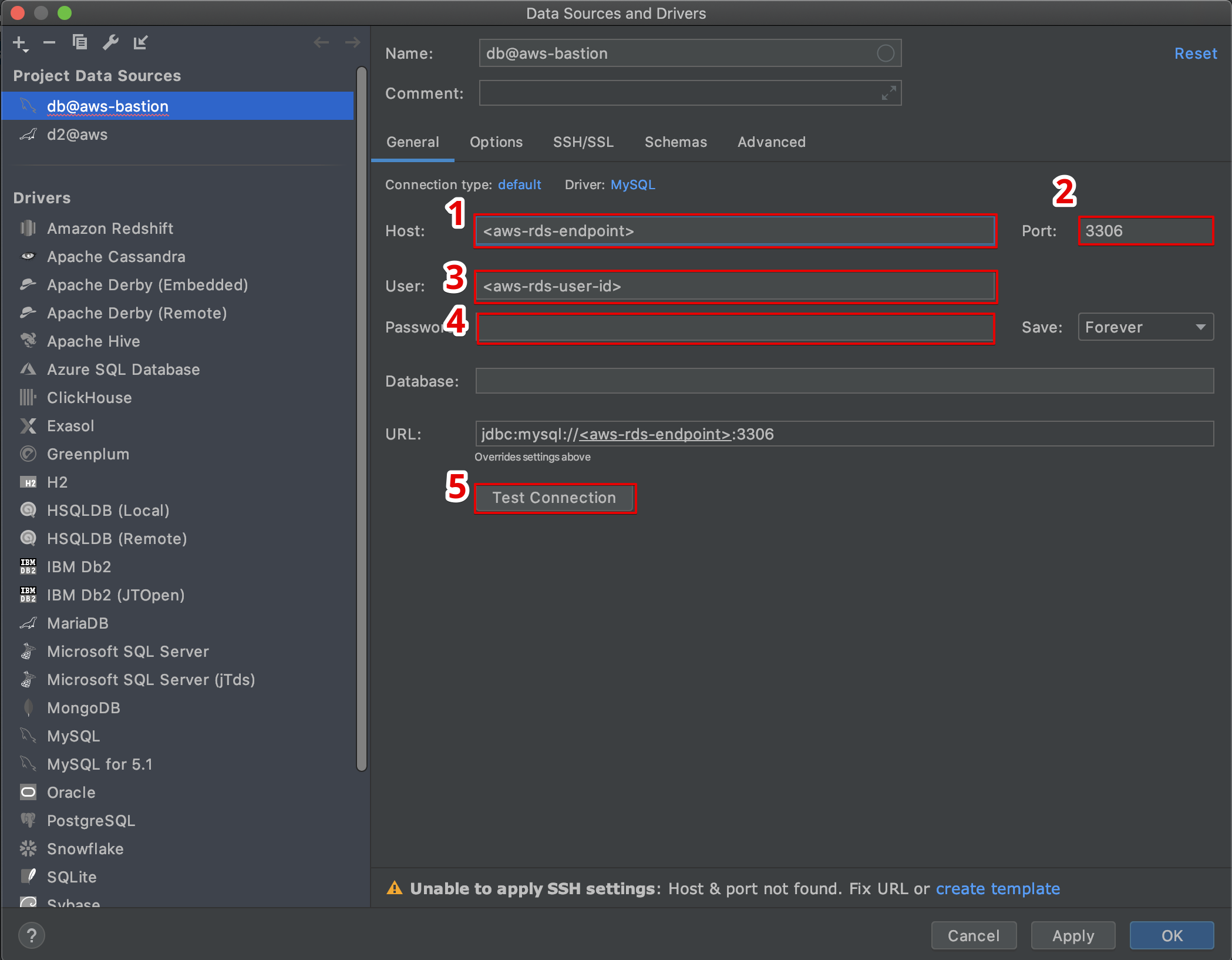
Connecting securely to IoT devices has become a cornerstone of modern cloud infrastructure, and AWS IoT SSH Tunnel is a game-changer in this domain. This innovative feature allows users to establish secure, encrypted connections between IoT devices and remote servers, enabling seamless management and troubleshooting. With the rise of IoT applications, businesses and developers need reliable tools to ensure secure access without compromising performance. AWS IoT SSH Tunnel bridges this gap by providing a robust, scalable solution that integrates seamlessly with AWS's ecosystem.
For those unfamiliar with the concept, AWS IoT SSH Tunnel leverages the power of AWS IoT Core to create secure communication channels. This feature is particularly beneficial for developers and administrators managing distributed IoT devices, as it eliminates the need for complex network configurations. By using AWS-managed infrastructure, users can focus on their core tasks while ensuring their devices remain secure and accessible. This article will explore the intricacies of AWS IoT SSH Tunnel, its benefits, and how it can be implemented effectively.
As we delve deeper into this guide, you'll discover the technical underpinnings of AWS IoT SSH Tunnel, its real-world applications, and best practices for implementation. Whether you're a seasoned AWS user or just beginning your IoT journey, this article aims to equip you with the knowledge and tools necessary to harness the full potential of AWS IoT SSH Tunnel. By the end, you'll have a clear understanding of how this feature can enhance your IoT infrastructure and streamline your workflows.
Read also:Juan Soler The Cinematic Legacy And His Remarkable Film Contributions
Table of Contents
- What is AWS IoT SSH Tunnel and How Does It Work?
- Why Should You Use AWS IoT SSH Tunnel for Secure Connections?
- Step-by-Step Guide to Setting Up AWS IoT SSH Tunnel
- How to Troubleshoot Common Issues with AWS IoT SSH Tunnel?
- What Are the Key Benefits of AWS IoT SSH Tunnel?
- Advanced Configurations for AWS IoT SSH Tunnel
- Real-World Use Cases of AWS IoT SSH Tunnel
- Frequently Asked Questions About AWS IoT SSH Tunnel
What is AWS IoT SSH Tunnel and How Does It Work?
AWS IoT SSH Tunnel is a secure communication feature that allows users to establish encrypted connections between IoT devices and remote servers. At its core, this feature utilizes AWS IoT Core, a managed cloud service that enables secure communication between connected devices and the cloud. By leveraging the Secure Shell (SSH) protocol, AWS IoT SSH Tunnel ensures that all data transmitted between devices and servers is encrypted, protecting sensitive information from unauthorized access.
The process begins when an IoT device initiates a connection request through AWS IoT Core. AWS then establishes a secure tunnel between the device and the remote server, using SSH to encrypt the communication channel. This tunnel allows administrators to securely access the device for tasks such as troubleshooting, software updates, or data retrieval. One of the standout features of AWS IoT SSH Tunnel is its ability to work seamlessly across firewalls and NATs, eliminating the need for complex network configurations.
For example, imagine a scenario where a manufacturing company needs to remotely update firmware on IoT sensors deployed in remote locations. Using AWS IoT SSH Tunnel, the company can securely connect to these devices without exposing them to the public internet. This not only enhances security but also simplifies the management of distributed IoT infrastructure. By integrating with AWS Identity and Access Management (IAM), users can also enforce granular access controls, ensuring that only authorized personnel can access the devices.
Why Should You Use AWS IoT SSH Tunnel for Secure Connections?
With the increasing reliance on IoT devices, securing remote access has become a top priority for businesses. AWS IoT SSH Tunnel offers a compelling solution by combining the robustness of AWS's infrastructure with the security of SSH. But what makes this feature stand out from other remote access tools? Let’s explore the reasons why AWS IoT SSH Tunnel is a preferred choice for secure connections.
First and foremost, AWS IoT SSH Tunnel eliminates the need for public IP addresses or open ports, which are common attack vectors for cybercriminals. By routing traffic through AWS IoT Core, the tunnel ensures that devices remain hidden from the public internet, significantly reducing the risk of unauthorized access. Additionally, the integration with AWS IAM allows administrators to define fine-grained access policies, ensuring that only authorized users can establish tunnels.
Another key advantage is scalability. AWS IoT SSH Tunnel is designed to handle millions of devices, making it suitable for both small-scale deployments and enterprise-grade IoT networks. Its seamless integration with other AWS services, such as AWS Lambda and Amazon S3, further enhances its utility. For instance, you can automate tasks like log collection or firmware updates by triggering AWS Lambda functions when a tunnel is established. This level of automation not only improves efficiency but also reduces operational overhead.
Read also:The Remarkable Life And Legacy Of Charles Xavier A Visionary Leader
How Does AWS IoT SSH Tunnel Compare to Traditional SSH?
Traditional SSH connections require devices to have public IP addresses or be accessible via port forwarding, which can be cumbersome and insecure. In contrast, AWS IoT SSH Tunnel simplifies this process by leveraging AWS's managed infrastructure. Here’s a quick comparison:
- Traditional SSH: Requires complex network configurations and exposes devices to potential attacks.
- AWS IoT SSH Tunnel: Uses AWS IoT Core to establish secure connections without exposing devices to the public internet.
Step-by-Step Guide to Setting Up AWS IoT SSH Tunnel
Setting up AWS IoT SSH Tunnel may seem daunting at first, but with a systematic approach, it becomes a straightforward process. This section provides a detailed walkthrough to help you configure AWS IoT SSH Tunnel for your IoT devices.
Step 1: Prerequisites
Before you begin, ensure that you have the following prerequisites in place:
- An AWS account with access to AWS IoT Core.
- An IoT device registered in AWS IoT Core.
- AWS CLI installed and configured on your local machine.
Step 2: Create an IoT Thing
In the AWS Management Console, navigate to AWS IoT Core and create a new IoT Thing. This represents your IoT device in the AWS ecosystem. Assign a unique name and attach the necessary policies to grant permissions for establishing tunnels.
Step 3: Install AWS IoT Device SDK
Download and install the AWS IoT Device SDK on your IoT device. This SDK enables the device to communicate with AWS IoT Core and establish tunnels. Follow the installation instructions provided in the official AWS documentation.
Step 4: Configure SSH Access
On your remote server, ensure that SSH is configured to allow connections from the IoT device. You may need to update the SSH configuration file (sshd_config) to permit tunneling.
Step 5: Establish the Tunnel
Use the AWS CLI to create a secure tunnel. The command typically looks like this:
aws iotsecuretunneling open-tunnel --destination-config '{"thingName":"YourIoTThing"}'Once the tunnel is established, you can use SSH to connect to your IoT device securely.
How to Troubleshoot Common Issues with AWS IoT SSH Tunnel?
Despite its robustness, AWS IoT SSH Tunnel can encounter issues that may disrupt connectivity. Fortunately, most problems can be resolved with a systematic troubleshooting approach. Here are some common issues and their solutions:
Issue 1: Tunnel Not Established
If the tunnel fails to establish, verify the following:
- Ensure that the IoT device is registered in AWS IoT Core and has the necessary permissions.
- Check the AWS CLI configuration to confirm that it is pointing to the correct AWS region.
- Review the IAM policies to ensure they allow the creation of secure tunnels.
Issue 2: SSH Connection Fails
If you can establish the tunnel but cannot connect via SSH, consider the following:
- Verify that the SSH service is running on the remote server.
- Check the SSH configuration file for any restrictions on tunneling.
- Ensure that the SSH key pairs are correctly configured on both the client and server.
What Should You Do If Logs Are Missing?
Missing logs can make troubleshooting more challenging. To address this, enable logging for AWS IoT Core and SSH. You can configure AWS CloudWatch to capture logs related to tunnel creation and SSH activity. This will provide valuable insights into the root cause of the issue.
What Are the Key Benefits of AWS IoT SSH Tunnel?
AWS IoT SSH Tunnel offers numerous benefits that make it an indispensable tool for managing IoT devices. From enhanced security to simplified operations, this feature provides value across multiple dimensions.
One of the most significant advantages is improved security. By eliminating the need for public IP addresses or open ports, AWS IoT SSH Tunnel reduces the attack surface for cybercriminals. Additionally, the integration with AWS IAM allows administrators to enforce strict access controls, ensuring that only authorized users can establish tunnels. This level of security is particularly crucial for industries like healthcare and finance, where data privacy is paramount.
Another key benefit is operational efficiency. AWS IoT SSH Tunnel simplifies the management of distributed IoT devices by providing a centralized, secure access point. This reduces the complexity of network configurations and minimizes the risk of human error. Furthermore, the ability to automate tasks using AWS Lambda enhances productivity and reduces operational costs.
Advanced Configurations for AWS IoT SSH Tunnel
For users looking to maximize the potential of AWS IoT SSH Tunnel, advanced configurations can unlock additional capabilities. These configurations enable features like multi-region support, custom IAM policies, and integration with third-party tools.
Multi-Region Support
AWS IoT SSH Tunnel supports multi-region deployments, allowing users to establish tunnels across different AWS regions. This is particularly useful for global IoT networks, as it ensures low-latency connections and high availability. To enable multi-region support, configure the AWS CLI to use the appropriate region endpoints when creating tunnels.
Custom IAM Policies
By creating custom IAM policies, you can define granular access controls for AWS IoT SSH Tunnel. For example, you can restrict tunnel creation to specific users or groups, or limit the duration of tunnels to enhance security. Custom policies can also be used to enforce compliance with organizational policies.
Real-World Use Cases of AWS IoT SSH Tunnel
AWS IoT SSH Tunnel has been successfully implemented in various industries, demonstrating its versatility and effectiveness. Here are some real-world examples:
- Smart Agriculture: Farmers use AWS IoT SSH Tunnel to remotely monitor and manage IoT sensors deployed in fields. This enables real-time data collection and analysis, improving crop yields and resource efficiency.
- Healthcare: Hospitals leverage AWS IoT SSH Tunnel to securely access medical devices, ensuring patient data remains confidential while enabling remote diagnostics and maintenance.
- Manufacturing: Manufacturers use this feature to troubleshoot IoT-enabled machinery on production lines, reducing downtime and improving operational efficiency.
Frequently Asked Questions About AWS IoT SSH Tunnel
How Secure Is AWS IoT SSH Tunnel?
AWS IoT SSH Tunnel uses industry-standard encryption protocols to secure data in transit. Additionally, its integration with AWS IAM ensures that only authorized users can establish tunnels, further enhancing security.
Can AWS IoT SSH Tunnel Be Used with Third-Party Devices?
Yes, AWS IoT SSH Tunnel is compatible with third-party devices as long as they are registered in AWS IoT Core and have the necessary SDKs installed.
Is AWS IoT SSH Tunnel Suitable for Large-Scale Deployments?
Absolutely. AWS IoT SSH Tunnel is designed to handle millions of devices, making it ideal for enterprise-grade IoT networks.
In conclusion, AWS IoT SSH Tunnel is a powerful tool that addresses the challenges of secure remote access for IoT devices. By leveraging AWS's managed infrastructure and the robustness of SSH, it provides a scalable, secure, and efficient solution for managing distributed IoT networks. Whether you're a developer, administrator, or business owner, mastering AWS IoT SSH Tunnel can significantly enhance your IoT infrastructure and streamline your workflows.