Imagine being able to control your IoT devices from anywhere in the world, all through the power of a Raspberry Pi and a free Android app. This innovative combination has revolutionized the way we interact with smart devices, offering unprecedented flexibility and control. Whether you're a seasoned developer or a curious tech enthusiast, understanding how to establish secure remote connections through SSH can unlock a world of possibilities for your IoT projects. The integration of these technologies represents a significant leap forward in home automation and remote device management.
As our homes and workplaces become increasingly connected, the need for reliable remote access solutions has never been greater. The Raspberry Pi, with its remarkable versatility and affordability, has emerged as a leading platform for IoT development. When paired with Android's widespread availability and robust ecosystem, users can create powerful, cost-effective solutions for managing their smart devices. This article will guide you through the essential steps and considerations for setting up secure remote access to your IoT devices, helping you harness the full potential of these technologies.
The significance of mastering remote SSH connections extends beyond mere convenience. In today's fast-paced world, the ability to monitor and control your IoT devices from anywhere can enhance security, improve efficiency, and provide peace of mind. From adjusting your home thermostat while on vacation to monitoring industrial sensors across multiple locations, the applications are virtually limitless. As we delve deeper into this topic, we'll explore the technical aspects, practical implementations, and innovative solutions that make remote IoT management not just possible, but remarkably straightforward.
Read also:Exploring Cristin Miliotis Husband And Personal Life A Closer Look
Table of Contents
- What Are the Fundamentals of IoT Device Remote SSH?
- How Can Raspberry Pi Enhance Your IoT Setup?
- What Are the Best Free Android Solutions for Remote SSH?
- How to Secure Your IoT Device Remote SSH Connections?
- What Are the Advanced Features of IoT Device Remote SSH?
- How to Troubleshoot Common Issues with IoT Device Remote SSH?
- IoT Device Remote SSH Raspberry Pi Free Android Integration
- What Are the Future Trends in IoT Remote Management?
What Are the Fundamentals of IoT Device Remote SSH?
When we talk about IoT device remote SSH, we're discussing a powerful protocol that enables secure communication between your devices. The SSH (Secure Shell) protocol has become the gold standard for remote administration, especially in IoT environments where security is paramount. This technology allows you to establish encrypted connections to your devices, regardless of their physical location, ensuring that your data remains protected during transmission.
At its core, SSH operates through a client-server architecture, where the client (your Android device, for instance) initiates a connection to the server (your Raspberry Pi). This connection is secured through robust encryption algorithms that protect both the authentication process and the subsequent data transfer. The protocol supports various authentication methods, including password-based and key-based authentication, with the latter being strongly recommended for enhanced security.
For IoT device management, SSH offers several crucial advantages. First and foremost, it provides a secure channel for executing commands and transferring files between devices. This capability becomes particularly valuable when managing multiple IoT devices spread across different locations. Additionally, SSH supports port forwarding and tunneling, allowing you to access services running on your IoT devices that might not be directly exposed to the internet. The protocol's versatility extends to supporting various operating systems and platforms, making it an ideal choice for heterogeneous IoT environments.
Understanding the IoT Ecosystem
The Internet of Things (IoT) ecosystem comprises numerous interconnected devices working together to achieve specific objectives. These devices range from simple sensors to complex industrial equipment, all communicating through various protocols and networks. In this interconnected web, secure remote access becomes crucial for maintaining system integrity and functionality.
IoT devices typically operate within a layered architecture that includes sensors and actuators at the edge, gateways for data aggregation, and cloud platforms for processing and storage. SSH plays a vital role in this architecture by providing secure access to different layers of the system. For instance, administrators can use SSH to securely access edge devices for configuration changes or firmware updates, while also maintaining secure connections to gateway devices and cloud servers.
The integration of SSH with IoT devices brings several technical considerations. Device manufacturers must implement SSH servers that are optimized for resource-constrained environments, ensuring minimal impact on device performance. Additionally, proper key management and certificate authorities become essential for maintaining a secure network of interconnected devices. As IoT networks grow in complexity, the ability to establish secure, authenticated connections between devices becomes increasingly critical for maintaining system security and operational efficiency.
Read also:Exploring The Life And Legacy Of Sawyer From Lost A Detailed Overview
How Does SSH Secure Your Connections?
SSH employs multiple layers of security to protect your IoT device connections. At the heart of its security framework lies strong encryption algorithms that ensure confidentiality and integrity of data in transit. When you establish an SSH connection to your Raspberry Pi, the protocol first negotiates a secure channel using a combination of symmetric and asymmetric encryption methods.
The authentication process in SSH is particularly robust, offering multiple layers of verification. While password-based authentication is supported, key-based authentication provides significantly enhanced security. This method involves generating a public-private key pair, where the public key is stored on the server (Raspberry Pi) and the private key remains securely on your Android device. The mathematical relationship between these keys ensures that only authorized devices can establish connections.
Beyond basic authentication, SSH incorporates additional security features such as host key verification, which protects against man-in-the-middle attacks. Each SSH server has a unique host key that clients verify during the initial connection. This verification process ensures that you're connecting to the legitimate server and not an imposter. Furthermore, SSH supports various encryption algorithms, allowing administrators to choose the most secure options compatible with their devices. The protocol also includes mechanisms for secure file transfer (SFTP) and port forwarding, extending its security benefits to various use cases in IoT management.
How Can Raspberry Pi Enhance Your IoT Setup?
The Raspberry Pi has emerged as a cornerstone in modern IoT implementations, offering an unparalleled combination of affordability, versatility, and performance. This credit-card-sized computer packs enough power to serve as a central hub for your IoT devices while maintaining low power consumption. Its ARM-based architecture and Linux operating system make it an ideal platform for running various IoT services and applications.
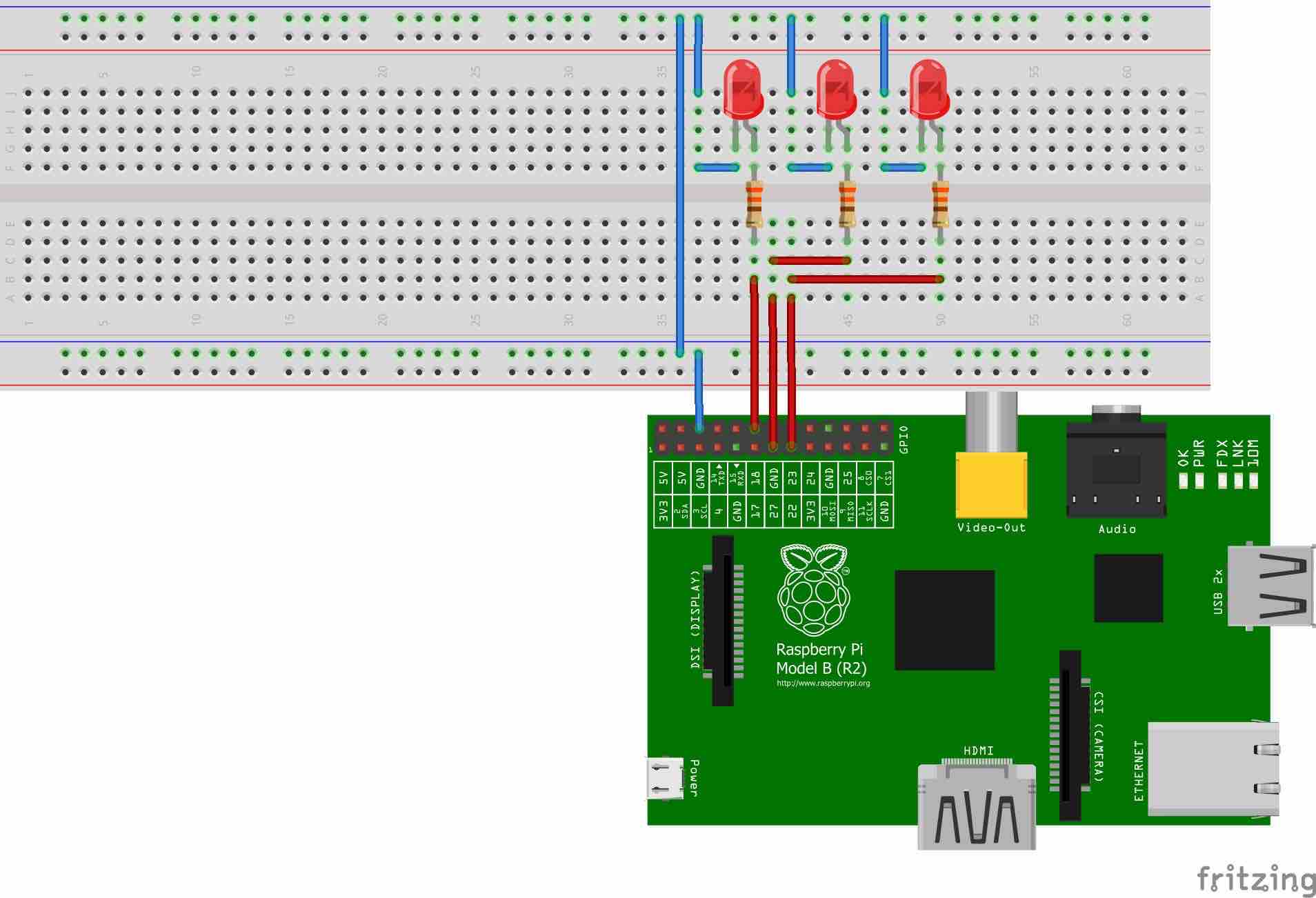
What sets Raspberry Pi apart in IoT deployments is its extensive connectivity options. The device typically features multiple USB ports, Ethernet connectivity, and wireless capabilities, allowing it to interface with various sensors and peripherals. Additionally, the GPIO (General Purpose Input/Output) pins provide direct hardware interfacing capabilities, enabling physical connections to custom circuits and sensors. This flexibility makes it possible to create sophisticated IoT solutions without requiring additional hardware components.
For remote SSH access, Raspberry Pi offers several advantages. Its lightweight operating systems, such as Raspberry Pi OS, are optimized for minimal resource usage while providing full SSH server capabilities. The device's low power requirements make it suitable for continuous operation, even in remote locations. Furthermore, the extensive community support and vast library of available software packages simplify the implementation of complex IoT functionalities, from data processing to device management.
Raspberry Pi as an IoT Hub
When configured as an IoT hub, Raspberry Pi serves as the central nervous system of your smart device network. This role involves managing device communication, processing sensor data, and providing a secure gateway for remote access. The device's ability to run multiple services simultaneously makes it particularly well-suited for this purpose, allowing it to handle various tasks without performance degradation.
The Raspberry Pi's processing capabilities enable local data processing and decision-making, reducing dependency on cloud services and minimizing latency. This local processing can include data aggregation, filtering, and initial analysis before forwarding relevant information to cloud platforms or other systems. The device's support for various programming languages and frameworks allows developers to implement complex logic and automation rules directly on the hub.
Security features on Raspberry Pi can be enhanced through various methods. The device supports full disk encryption, secure boot processes, and various firewall configurations. When combined with SSH for remote access, these security measures create a robust foundation for managing IoT devices. Additionally, the Raspberry Pi's ability to run containerized applications allows for isolated environments for different services, further enhancing security and stability in IoT deployments.
Optimizing Raspberry Pi for Remote Access
To maximize the effectiveness of remote SSH access on Raspberry Pi, several optimization steps should be considered. First and foremost, it's crucial to keep the operating system and all installed packages up to date. Regular updates ensure that security patches are applied and that the system remains compatible with the latest SSH protocols and encryption standards.
Performance optimization begins with proper configuration of the SSH server. This includes adjusting connection settings, configuring resource limits, and implementing connection rate limiting to prevent denial-of-service attacks. Additionally, enabling compression for SSH connections can improve performance, especially when transferring large files or working with resource-constrained devices.
For enhanced reliability, consider implementing monitoring and alerting systems on your Raspberry Pi. These systems can notify you of potential issues, such as high CPU usage or failed login attempts, allowing for proactive maintenance. Furthermore, configuring proper logging and log rotation ensures that you maintain a record of system activities without consuming excessive storage space. The use of tools like fail2ban can automatically block suspicious IP addresses, adding an extra layer of security to your remote access setup.
What Are the Best Free Android Solutions for Remote SSH?
The Android ecosystem offers several excellent free applications for establishing SSH connections to your IoT devices. These applications provide intuitive interfaces while maintaining the robust security features required for managing remote devices. Among the most popular options, Termius, JuiceSSH, and ConnectBot stand out for their comprehensive feature sets and reliability.
Termius offers a particularly user-friendly experience with its clean interface and powerful features. The free version includes essential SSH functionality, multiple host support, and secure key management. Its intuitive design makes it accessible for beginners while still offering advanced features for experienced users. JuiceSSH, another popular choice, provides similar capabilities with additional customization options and support for various authentication methods.
ConnectBot, being one of the earliest SSH clients for Android, remains a reliable option with its straightforward approach and minimal resource requirements. While it may lack some of the more advanced features found in newer applications, its stability and simplicity make it an excellent choice for basic remote management tasks. All these applications support key-based authentication and offer secure storage for your connection details, ensuring that your remote access remains both convenient and secure.
How to Secure Your IoT Device Remote SSH Connections?
Securing your IoT device remote SSH connections requires a comprehensive approach that addresses multiple potential vulnerabilities. The first line of defense involves implementing strong authentication mechanisms that go beyond simple password protection. Key-based authentication should be mandatory for all connections, with private keys stored securely on your Android device using the built-in keystore or dedicated password manager applications.
Network security plays a crucial role in protecting your SSH connections. Implementing proper firewall rules on both your Raspberry Pi and network gateway can significantly reduce the attack surface. Consider using non-standard ports for SSH connections to avoid automated attacks targeting the default port 22. Additionally, configuring IP whitelisting or using VPN solutions can further restrict access to authorized devices only.
Regular security audits and monitoring are essential for maintaining the integrity of your remote connections. Implementing intrusion detection systems and regularly reviewing access logs can help identify potential security threats before they become serious issues. Furthermore, maintaining up-to-date backups of your configuration files and critical data ensures that you can quickly recover from any security incidents that might occur.
Implementing Strong Authentication Methods
Strong authentication methods form the foundation of secure remote SSH access.